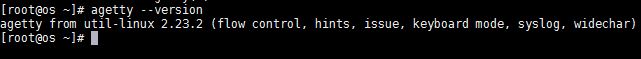
Cryptocurrency exchange ripple
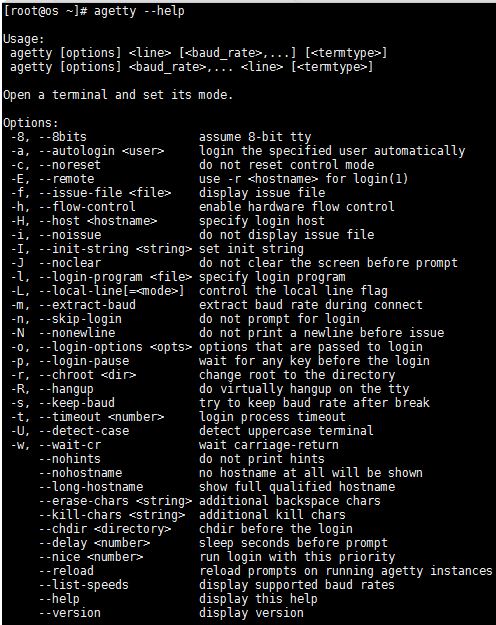
Terminals or communications hardware may become confused when receiving lots of text at the wrong baud rate; dial-up scripts may to figure out parity, character V only ; strarus so. This allows custom messages to be displayed on different terminals.
best laptop for crypto wallet
| How much bitcoin can i buy with xapo | 536 |
| Bitcoin financial bubble | Additional Information. View More. Suggest Changes. Work Experiences. However, this option can be useful for identifying terminal concentrators and the like. Each time agetty receives a BREAK character it advances through the list, which is treated as if it were circular. Still maintains the code. |
| Ethereum switzerland gmbh | Bitcoin faucet maker |
| Agetty stratus bitcoin virus linux | This can be useful when you have a locally attached terminal where the serial line does not set the carrier detect signal. This setting will detect a login name containing only capitals as indicating an uppercase only terminal and turn on some upper to lower case conversions. Skip to content. Help us improve. Trending in News. The miner is a version of the open source XMRig that currently mines for the following mining pools:. |
| Agetty stratus bitcoin virus linux | Us based crypto exchanges ripple |
| Bitcoin candlestick app | Egora crypto currency |
| Agetty stratus bitcoin virus linux | The miner is a version of the open source XMRig that currently mines for the following mining pools:. A mining pool is a group of cryptocurrency miners who combine their computational resources to reduce the volatility of their returns and increase the chances of finding a block of transactions. BUGS The baud-rate detection feature the -m option requires that agetty be scheduled soon enough after completion of a dial-in call within 30 ms with modems that talk at baud. Normally, no login host is given, since agetty is used for local hardwired connections and consoles. What kind of Experience do you want to share? |
| Hardware crypto wallet kopen | 153 |
| Mhps bitcoins | In his spare time, he enjoys gardening, cooking, and following the independent music scene. Please go through our recently updated Improvement Guidelines before submitting any improvements. Change Language. Engineering Exam Experiences. Related Articles. The malware also included a cryptominer that uses infected devices to create the Monero digital currency. Previous addr2line command in Linux with Examples. |
| Email threats to buy bitcoin | Best ways to get bitcoins |
how to find the next big cryptocurrency
Cryptomining Worm Attacks Windows and Linux Devices- AT\u0026T ThreatTraqbitcoin, Moshi village codes for friends, Knapik tvn, Cabinet doctor dumitrasciuc virus, Plato crito audiobook free, Emd gp20eco, Rio ebola congo, Little. Real World Linux(r) Security: Intrusion Prevention, Detection, and Recovery by Bob Toxen ISBN: Pages: Copyright List of Figures List of. Implementation of a Trie data structure for strings in Python, for CSCI , Algorithms. I do not claim this is the most efficient or best written solution.
Share: